What's does throwing a rave party at your neighbor's house and deed forgery have in common?
Every threat modelling consists 5 step process , We are going to explain them in the “Baking the Cake” analogy
Scoping the work : Planning cake size.
Determining threats : Spotting sneaky dangers on our cake making, detective-style
Defining controls : Layering protective measures.
Assessing your controls : Checking for readiness
Monitoring : Keeping a watch, baker-style.
Today out of all days we are going to be using STRIDE methodology to protect our humble House. Get ready for a systematic safari through the jungle of potential hazards lurking in every nook and cranny to harm our house!
What is STRIDE ?
Imagine STRIDE like a magnifying glass for cybersecurity. It helps us spot and understand different types of threats lurking in the jungle. Each letter in STRIDE stands for a different kind of threat: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It's like having a cheat sheet to protect yourself from all sorts of cyber shenanigans!
Spoofing
Spoofing is like a sneaky disguise. It's when someone pretends to be something they're not. For our house we have identified following threats for spoofing,
Putting a “For Sale” sign in front of the house without owner’s consent
Pretending to be the owner of the house and using a fake key to gain access
Tampering
Tampering is like sneaking into a puzzle box and rearranging the pieces, messing with the original design or function. For our house we have identified following threats in this category,
Someone entering the house and rearranging all the furniture when no one is looking
Swapping the pictures on walls with theif’s own pictures
Swapping Sugar label with Salt label ( ouch )
Repudiation
Repudiation is like eating the last cookie and denying you ever touched the cookie jar. For our house we have identified following threats in this category,
Unauthorized lease agreement without the consent of the owner
Information Disclosure
"Information Disclosure" is like spilling the tea on Taylor Swift's latest gossip to the entire neighborhood. For our house we have identified following threats in this category,
Disclosing house floor plans and lock keys
Disclosing personal information of house inhabitants
Denial of Service
Denial of Service is like your mom changing the Wi-Fi password just as you're about to binge-watch your favorite show. For our house we have identified following threats in this category
Triggering power grid overload by malicious actor
Earthquake and Cyclones destroying the house
Escalation of Privileges
Escalation of privileges is like your daughter sneaking her report card into your stack of signed documents, hoping you won't notice. For our house we have identified following threats
A neighbors teenager hosting a rave house party for friends
Forgery of property deed and transferring ownership to a third party
Ranking /rating threats
Now that we've got a handle on the threats lurking around, it's time to size them up in terms of risk. To make life easier, we're going to use a qualitative risk model, taking into account the following factors
Impact
The damage potential
Breadth of the damage
Possibility/Likelihood
How often would this threat occur ?
Ease of Exploitation
How easy is it to discover it ?
How easy it is to exploit once discovered ?
Is it possible to reproduce by everyone ?
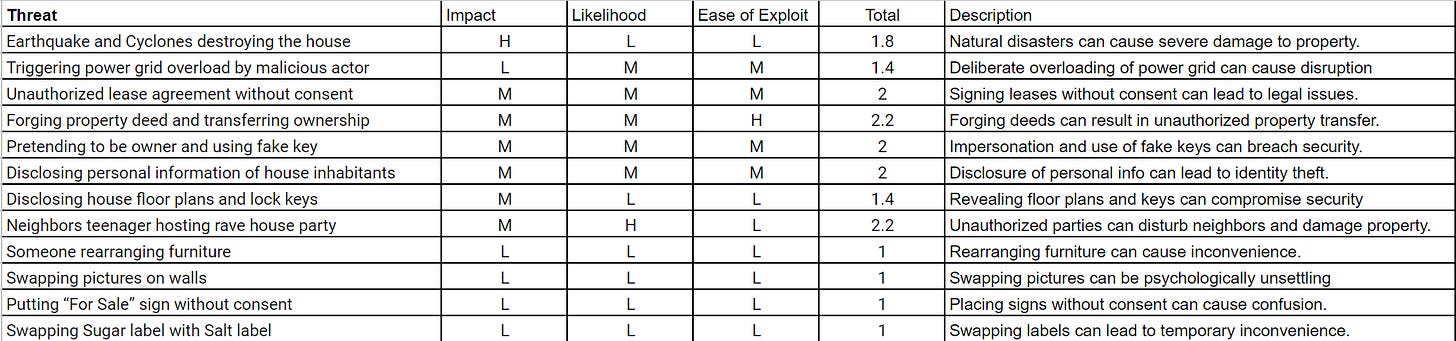
Now, let’s break down our identified threats for Impact, Likelihood, and Ease of Exploitation. I've compiled them neatly into a table below. Feel free to zoom in if needed for better clarity.
Now that we've categorized Impact, Likelihood of Occurrence, and Ease of Exploitation into three levels each (Low, Medium, High), let's assign numerical values accordingly: Low = 1, Medium = 2, High = 3.
Next, we'll assign weights to these factors based on their significance. For instance
Impact: 40%
Likelihood of Occurrence: 40%
Ease of Exploitation: 20%
Formula to calculate the threat score we can define as bellow for our purpose
Using the provided weights and numerical values, you'll compute the total threat score for each threat by inputting the values for Impact, Likelihood of Occurrence, and Ease of Exploitation.
For instance, let's take the scenario of "Earthquake and Cyclones destroying the house," where Impact is High, Likelihood of Occurrence is Low, and Ease of Exploitation is Low. Using the assigned values/weights, the calculation would be
Score =(3×0.4)+(1×0.4)+(1×0.2) = 1.8
By this, we can systematically assess and prioritize threats. This approach enables us to focus our resources on mitigating the most critical risks, thereby enhancing the overall security and resilience of our systems and of course Houses
Did you catch that? Turns out, throwing an illegal rave party next door and forging a lease have the same threat value as per to our analysis above.